-
- Jun 22
-
Macalegin Electronics

- 0
What is a Stingray Attack?
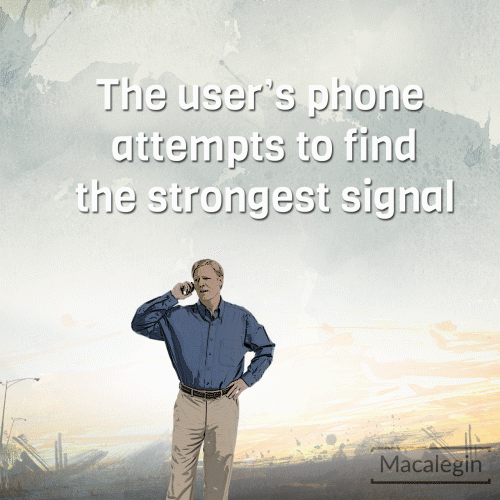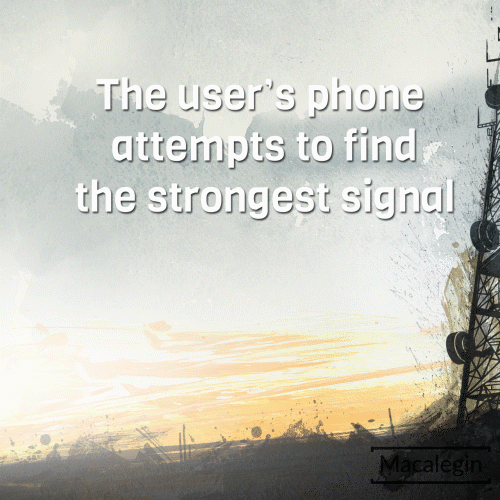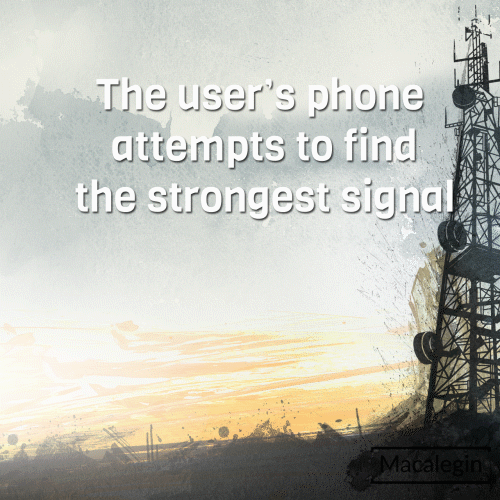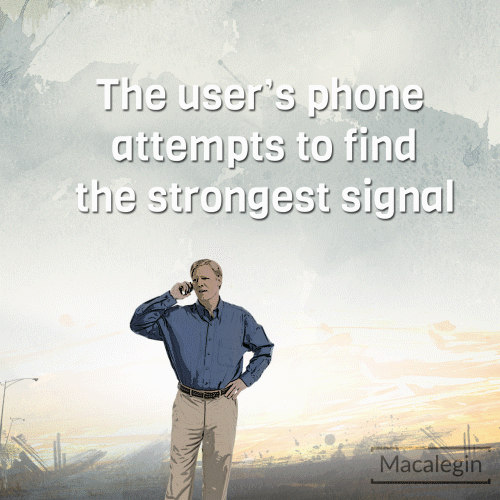
Your phone or mobile device can be tricked into connecting with a fake cell tower or StingRay device.
Devices typically seek out the strongest signal for the best mobile connection. A stingray device exploits this function by pushing out a signal stronger than nearby towers tricking devices in the radius to connect to them instead. When your device sees the stingray signal it thinks that that is the strongest “tower” to connect to and then connects to the stingray instead of an actual network tower.
The StingRay device is an IMSI-catcher with passive (digital analyzer) and active (cell-site simulator) capabilities. The active mode is where it pushes out a stronger signal to gain device connections. The active mode also can:
- Extracting stored data such as International Mobile Subscriber Identity (“IMSI”) numbers and Electronic Serial Number (“ESN”),[14]
- Writing cellular protocol metadata to internal storage
- Forcing an increase in signal transmission power,[15]
- Forcing an abundance of radio signals to be transmitted
- Interception of communications content
- Tracking and locating the cellular device user,[9]
- Conducting a denial of service attack
- Encryption key extraction.[16]
- Radio jamming for either general denial of service purposes[17] or to aid in active mode protocol rollback attacks
(source Wikipedia article located here.)

Built to be a Government & Military Tool
This technology is aimed at and offered to government/military but it can be scary for consumers to think about how it could be used in the wrong hands. The original research and development of the StingRay and similar tech were likely to help with military efforts. In Afghanistan coalition forces were engaging an enemy using fabricated explosives triggered often by cell phones so arming the ground forces with the ability to disrupt, locate and track individuals using these phones around forces was beneficial.
Device Size and Location Vary
Our animated visual shows the Stingray Device as a normal tower but the actual device could be a system installed in a vehicle or in the military some systems could be used in a backpack. The point is you won’t necessarily know anything is wrong as the phone would think it is connected to a normal cell tower. It looks like the transition to 5g networks will help protect users from these fake mobile base stations or StingRays, you can learn more about 5g here.

